|
 |
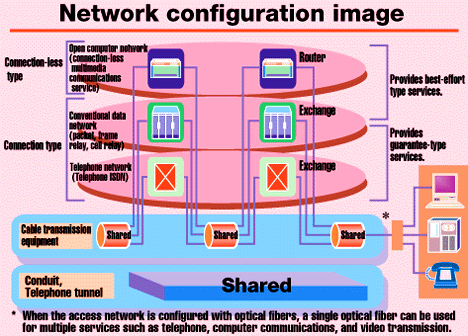
 Configuration of new network
Configuration of new network
(Open Computer Network) |
 |
- The network demanded for secure communication is different in service quality from the network focusing on its cheap charge rather than quality.
- The two networks are based on different protocols.
- The full-fledged network and the young one are different both in node capacity and in growth speed.
Consisting of nodes independent of existing telephone networks and conventional data networks